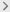We assess the security of your entire digital environment, including infrastructure, servers, operating systems, websites, mobile apps, and cloud storage, to identify vulnerabilities and mitigate potential risks to your business.
Testing processes include:
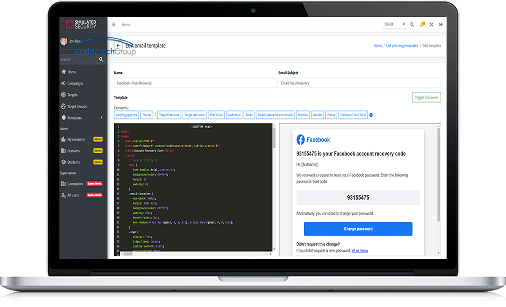
Penetration Testing: Finding security weaknesses by simulating real cyberattacks on your company's systems, networks, or applications.
Vulnerability Assessment: Identifying, analyzing, and prioritizing security weaknesses.
Attack Surface Discovery: Discovering all possible entry points that could be exploited by attackers.
Phishing Simulation: Testing employees by sending fake phishing emails to assess their awareness and response to potential threats.
Penetration Testing
Simulating real-world attacks to uncover and address vulnerabilities before they can be exploited.
Vulnerability Assessment
Systematically identifying and prioritizing security weaknesses across your assets.
Attack Surface Discovery
Mapping all external and internal exposure points to minimize attack opportunities.
Phishing Simulations
Testing employee awareness and resilience against social engineering attacks.

We implement the necessary procedures to fix and protect the weaknesses. We deploy protection software and automate security processes for you.
Our comprehensive approach includes:
Security Audits: Identifying and addressing security gaps to enhance your organization’s defenses.
Secure Coding Practices: Leveraging SAST, DAST, and SCA tools to ensure secure software development and deployment.
Automated Assessments: Implementing continuous scanning and asset management to monitor and control risks in real time.
Security Maturity Model Development: Building customized frameworks to measure, track, and improve your security capabilities.
Integrated Purple Team Operations: Enhancing threat detection and response through collaborative use of Blue Team tools, simulated attacks, and intrusion testing.


We equip your team with the knowledge and skills to identify, prevent, and respond to security threats through practical, hands-on training customized for your organization.
Our training programs include:
Security Awareness: Educating employees to identify and mitigate cyber risks and attacks effectively.
Secure Coding Practices: Teaching developers how to write code that minimizes vulnerabilities.
Honeypots & Cybertraps: Demonstrating how to set up decoys to detect and analyze malicious activity.
OSINT & Threat Intelligence: Training on leveraging open-source intelligence to identify potential threats.
Penetration Testing Services: Equipping your team with skills to simulate real-world attacks and strengthen defenses.
Steps we take to conduct the penetration testing
 Identify weaknesses and enhance overall security
Identify weaknesses and enhance overall security Prevent financial loss and disruptions to business operations
Prevent financial loss and disruptions to business operations Secure sensitive data from theft or exposure
Secure sensitive data from theft or exposure Stop hackers from compromising your systems
Stop hackers from compromising your systems Builds stronger customer loyalty and trust in your business
Builds stronger customer loyalty and trust in your business Ensure compliance with industry standards and regulations
Ensure compliance with industry standards and regulationsSecurity assessment
Evaluate the security level of the current team/project
Attacks surface discovery
Discover all the assets belonging to the target and identify possible threats
Vulnerability assessment
Assess all assets and check them for known vulnerabilities
Implementing procedures
Patch, manage vulnerabilities, and train security hygiene awareness
Security maturity model
Deploy maturity model for future improvements and KPI tracking
Some of our clients


With over 1000 penetration tests and over 3000 employees trained in cybersecurity awareness workshops, our team will cover a complete cybersecurity package for you, including advanced tests, prevention and fixing operations, and employee training through various real-life simulations.
With certified security expertise, 24/7 support, and happy clients, Roweb is your go-to cybersecurity company to contact.






Assessments are also crucial when introducing new technology or equipment to ensure they do not bring additional vulnerabilities into the network.
Significant changes to applications, office relocations with new technical setups, or updates to internal policies and procedures all require careful evaluation to address potential security impacts.
Additionally, after applying security patches or implementing new solutions, assessments help confirm that these measures have been properly implemented.




Advanced technologies like AI-driven threat detection and Zero Trust architecture enhance defenses, while employee training ensures awareness of the latest risks.
We also regularly update policies and collaborate with vendors to further strengthen security. Additionally, we conduct simulations to ensure readiness to address threats effectively.